How To Configure SSL Host Headers in IIS 6
If you need to set up SSL Host Headers for IIS 7 instead of IIS 6, see SSL Host Headers in IIS 7.
Because of the way that the SSL protocol works, it is normally necessary to have a unique IP address for each SSL certificate that you are using. This is because the host header information that tells the server which website to serve up and therefore which SSL certificate to use is encrypted and can't be unencrypted unless it knows which SSL certificate to use. It's like the "chicken and egg" problem. The Apache web server documentation explains the problem clearly.
If you have to use the same IP address for multiple sites, one simple solution is to just use different port numbers. For example:
https://site1.mysite.com
https://site2.mysite.com:8081
https://myothersite.com:8082

But doing it this way requires that you always visit the site using the port number and always reference it in links with the port number.
There is a more elegant method, if you have IIS 6.0 or later. That method is to use SSL Host Headers.
With SSL Host Headers, you will essentially use one SSL certificate for all of the sites that use SSL on a particular IP address. For this to work then, you will need to have either a Wildcard certificate or a Unified Communications Certificate. If all of the websites are subdomains of one domain name (e.g. site1.mysite.com, site2.mysite.com), you can use a Wildcard certificate. If there are completely different domain names (e.g. mysite.com, myothersite.com), you will need to use a Unified Communications Certificate.
The first step, if you haven't already done it, is to set up each of the websites with normal http host header values. You can do this by clicking the Advanced button next to the IP address when editing each website's properties in IIS. Just click the Edit button and add a domain name as the host header value.

Next, you will need to create a pending request on one of the websites and order the Wildcard or UC certificate from the certificate authority of your choice. Once you have a Wildcard or UC certificate that will work for all of the hostnames that are on the same IP address, you need to use it to complete the pending request on the website that you created it on. Then you just need to configure the SecureBindings metabase property on each of the other sites so it contains the host header name of the site. To do so, follow these steps:
- Click Start, click Run, type
cmdin the Open box, and then click OK. - Navigate to your IIS scripts directory by typing
cd C:\Inetpub\AdminScriptsAdjust the path to where the adsutil.vbs file is, if necessary. - Type the following command at the command prompt:
cscript.exe adsutil.vbs set /w3svc/<site identifier>/SecureBindings ":443:<host header>"
<host header> is the host header value for the Web site (www.myothersite.com). <site identifier> is the IIS site ID displayed when looking at all the websites in IIS.
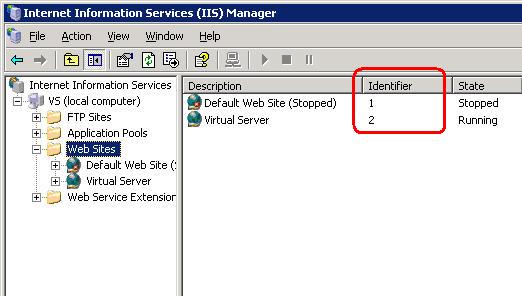
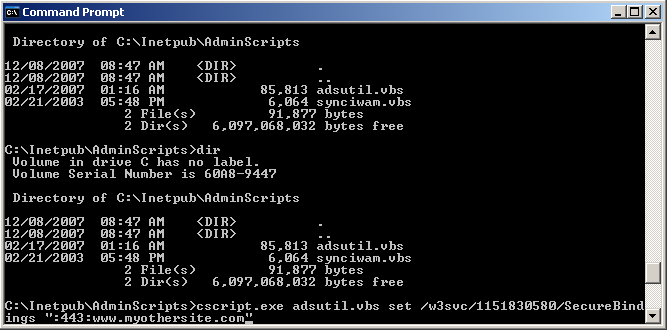
Run that command for each of the websites that need to use that certificate. They will then use the same certificate that was install to the first site on the IP. A few more notes about SSL Host Headers in IIS 6 can be found here.
Apache
This same basic functionality (using a single certificate for multiple websites on the same IP address) can be acheived in Apache by simply adding this line to your Apache configuration file:
NameVirtualHost 192.168.1.1:443
This essentially instructs Apache to use the SSL certificate in the first Virtual Host for that IP address on all the other virtual hosts for the same IP address. You just need to make sure to use a certificate that will cover the names of all the sites as discussed above. View a sample configuration file demonstrating this.
Different Certificates on the Same IP address
It is generally not possible to use different SSL certificates on the same IP address. However, a modification to the SSL protocol, called Server Name Indication, allows the domain name to be passed as part of the TLS negotiation allowing the server to use the correct certificate even if there are many different sites using different certificates on the same IP address and port. Server Name Indication is supported by most modern web browsers but only a few web servers, such as Apache, Lighttpd, and Nginx, support it using special add-ons.
If you're feeling adventurous you can try using different certificates on the same IP address with Apache using one of these tutorials:
- How To Enable Multiple HTTPS Sites For One IP On Debian Etch Using TLS Extensions
- SSL-enabled Name-based Apache Virtual Hosts with mod_gnutls
Originally posted on Sat Dec 8, 2007


Comments