XSS vulnerability found on PayPal
An XSS vulnerability has been discovered on a PayPal page that could enable attackers to make a fake page that steals users' personal information. Harry Sintonen, a researcher in Finland, discovered the flaw and revealed it to others in an IRC chat with other security professionals. The flaw could allow an attacker to easily put their own content on an authentic PayPal page that displays https://www.paypal.com in the address bar and even uses an EV SSL Certificate to turn the address bar green.
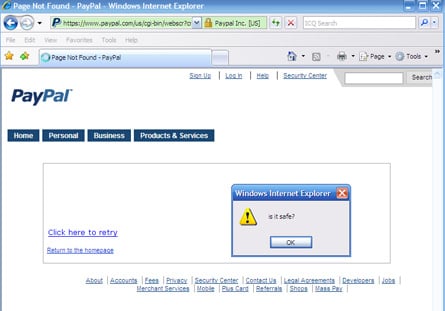
The question of whether EV Certificates make XSS vulnerabilities more harmful has been brought up several times before. It is especially important to consider when popular sites like PayPal and SourceForge are affected. Netcraft has been critical of EV Certificates when they are involved in XSS and noted how PayPal has been such a huge supporter of EV Certificates:
While SSL certificates do indeed provide a higher level of assurance when it comes to site ownership, they cannot guarantee that a site is free from other security problems – including cross-site scripting. There are concerns that hackers may exploit misunderstandings in the significance of the green address bar for their own benefit, piggybacking off the trust that is instilled by EV certificates. Users need to be aware that a green address bar does not guarantee the origin of a page's contents if there is a cross-site scripting vulnerability on that page.
The vulnerability comes to light only a month after PayPal published a practical approach to managing phishing on their blog, which extols the use of Extended Validation certificates in preventing phishing. The document describes browsers that do not support EV certificates as "unsafe" and announces the company's plans to block customers from accessing their website from the most unsafe browsers.
Dan Goodin even pointed out how EV Certificates seemed to fill an imaginary hole:
The discovery is one more reason to remain skeptical of extended validation SSL, which has always struck us as a solution in search of a problem. Yes, we know it's supposed to close a loophole that's long existed in SSL by certifying, in this case for example, that it is eBay (the parent company of PayPal) that owns the SSL certificate for the specific PayPal page. But we've not yet heard of a single attack involving a forged certificate, so we're tempted to think the measure is more gimmick designed to generate revenue for VeriSign and its competitors than anything else.Still, the effectiveness of EV Certificates in gaining user's trust is getting harder to dispute. The most effective approach to resolving problems like this is stressing complete security compliance by detecting and fixing XSS flaws or implementing a system in web browsers that requires all content on an EV protected page to come from sources that are also EV protected.
Originally posted on Sun May 18, 2008
